Okay, here’s an article about CRM with blacklist monitoring, targeting around 1200 words. I’ve aimed for a balance of informative and engaging content.
CRM with Blacklist Monitoring: Protecting Your Reputation and Boosting Customer Trust
In today’s interconnected and increasingly regulated business environment, Customer Relationship Management (CRM) systems are no longer just tools for managing customer interactions and sales pipelines. They’ve evolved into critical hubs for data security, compliance, and brand reputation management. One crucial aspect of this evolution is the integration of blacklist monitoring, a proactive measure that safeguards your business from potentially damaging interactions with individuals or entities flagged for suspicious or illegal activities.
The Growing Importance of Blacklist Monitoring
Blacklists, also known as sanction lists or watchlists, are databases containing information about individuals, organizations, or countries that have been identified as posing a risk. These lists are compiled by various government agencies, international organizations, and financial institutions to combat financial crime, terrorism, money laundering, and other illegal activities.
The consequences of doing business with a blacklisted entity can be severe, ranging from hefty fines and legal repercussions to significant reputational damage and loss of customer trust. Therefore, businesses must implement robust measures to identify and avoid these high-risk interactions. This is where CRM with integrated blacklist monitoring becomes essential.
What is CRM with Blacklist Monitoring?
CRM with blacklist monitoring combines the traditional functionalities of a CRM system – such as contact management, sales automation, and customer service – with the ability to automatically screen customer data against various blacklists in real-time. This integration provides a powerful layer of protection, helping businesses:
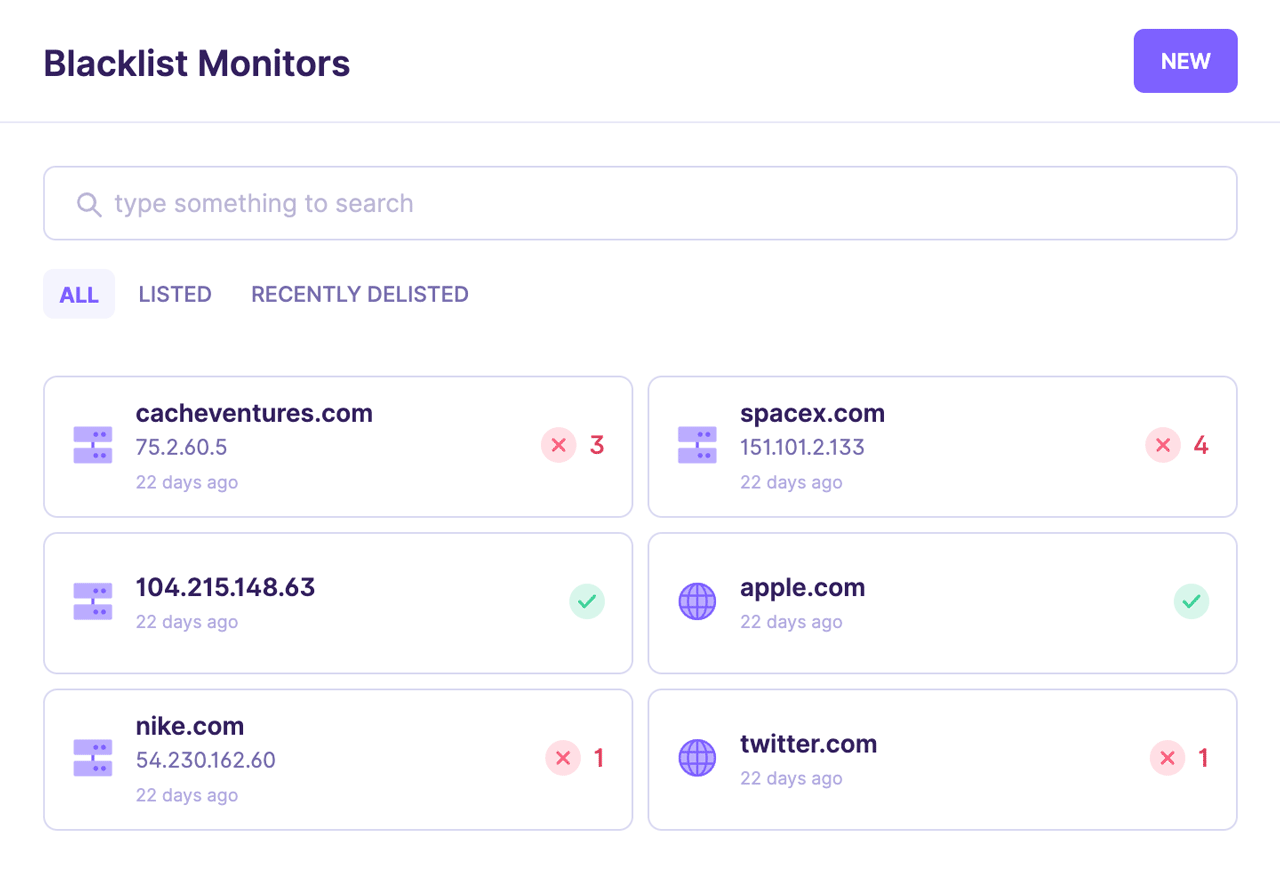
- Identify High-Risk Customers: Automatically flag individuals or organizations that appear on blacklists during the onboarding process or throughout the customer lifecycle.
- Prevent Financial Crime: Reduce the risk of being involved in money laundering, terrorist financing, or other illegal activities.
- Ensure Regulatory Compliance: Meet Know Your Customer (KYC) and Anti-Money Laundering (AML) requirements mandated by regulatory bodies.
- Protect Brand Reputation: Avoid association with individuals or entities that could damage your brand image.
- Minimize Legal Risks: Reduce the likelihood of facing legal penalties and lawsuits due to non-compliance.
How CRM Blacklist Monitoring Works
The integration of blacklist monitoring into a CRM system typically involves the following steps:
- Data Integration: The CRM system is connected to one or more blacklist data providers. These providers maintain and update their databases with information from various sources, including government agencies, law enforcement, and international organizations.
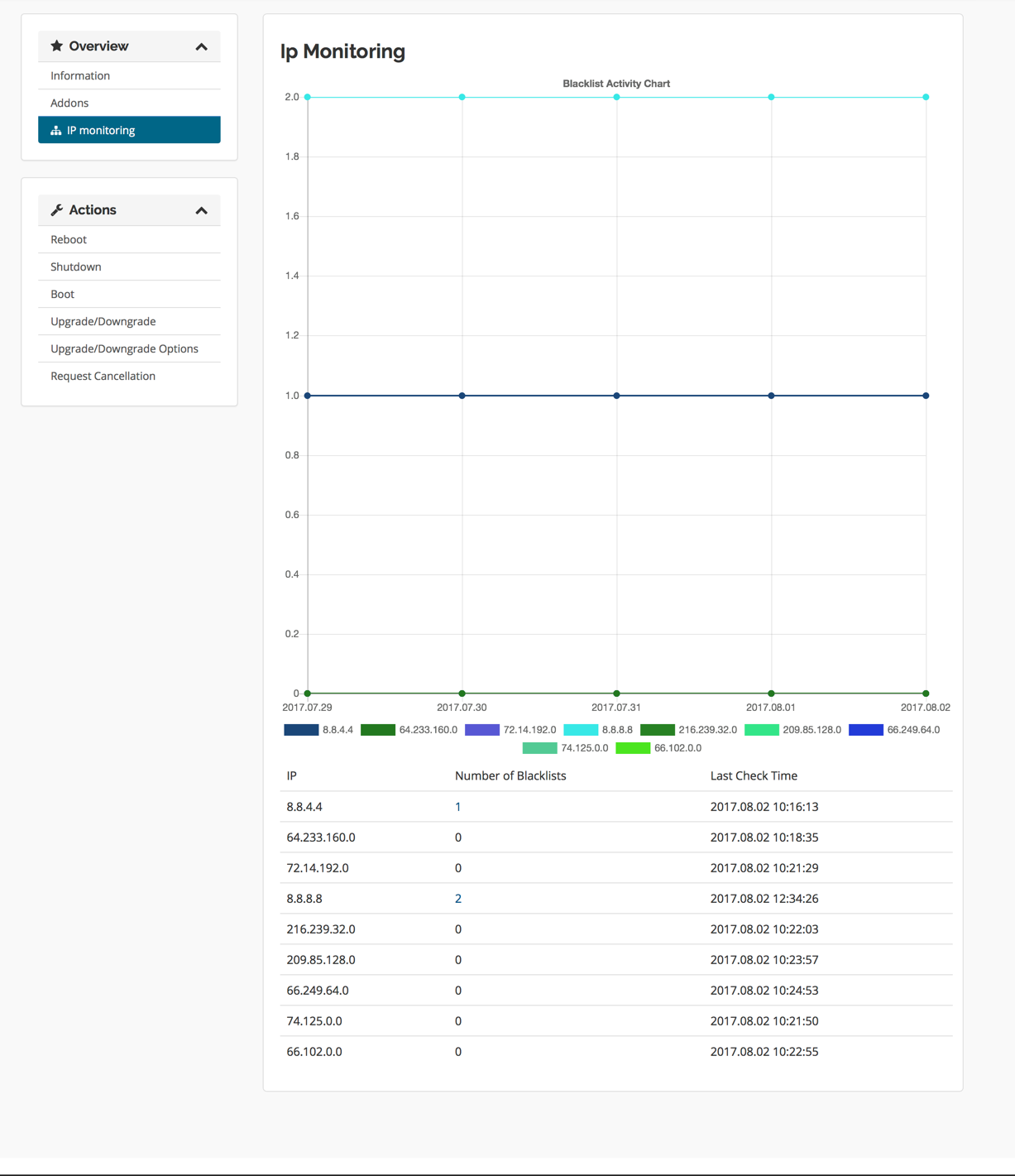
- Automated Screening: When new customer data is entered into the CRM or when existing customer data is updated, the system automatically screens the data against the blacklists. This screening process involves matching customer information, such as name, address, date of birth, and company registration details, against the entries in the blacklists.
- Real-time Alerts: If a match is found, the CRM system generates an alert, notifying the relevant personnel, such as compliance officers or customer service representatives. The alert typically includes details about the match, the specific blacklist, and the potential risk associated with the customer.
- Investigation and Due Diligence: Upon receiving an alert, the business must conduct further investigation and due diligence to verify the accuracy of the match and assess the level of risk. This may involve gathering additional information about the customer, reviewing transaction history, and consulting with legal counsel.
- Risk Mitigation: Based on the results of the investigation, the business can take appropriate risk mitigation measures. These measures may include refusing to onboard the customer, terminating the relationship, reporting the suspicious activity to the authorities, or implementing enhanced monitoring.
- Audit Trail and Reporting: The CRM system maintains an audit trail of all blacklist screening activities, including the dates and times of screenings, the results of screenings, and the actions taken in response to alerts. This audit trail is essential for demonstrating compliance with regulatory requirements and for providing evidence in the event of an investigation. The CRM can also generate reports on blacklist screening activity, providing insights into the overall risk profile of the customer base.
Key Features of a CRM with Blacklist Monitoring
When selecting a CRM with blacklist monitoring, consider the following key features:
- Real-time Screening: The system should be able to screen customer data against blacklists in real-time, ensuring that potential risks are identified as early as possible.
- Comprehensive Blacklist Coverage: The system should support a wide range of blacklists, including those from government agencies, international organizations, and financial institutions.
- Customizable Screening Rules: The system should allow you to customize the screening rules based on your specific risk appetite and regulatory requirements. This includes the ability to adjust the sensitivity of the matching algorithm and to define specific criteria for triggering alerts.
- Automated Alerts and Notifications: The system should automatically generate alerts and notifications when a match is found, ensuring that the relevant personnel are promptly informed.
- Detailed Audit Trail: The system should maintain a detailed audit trail of all blacklist screening activities, including the dates and times of screenings, the results of screenings, and the actions taken in response to alerts.
- Reporting and Analytics: The system should provide reporting and analytics capabilities, allowing you to track blacklist screening activity and identify trends in your customer base.
- Integration with Other Systems: The system should be able to integrate with other systems, such as your accounting software and payment gateway, to provide a holistic view of your customer relationships and transactions.
- User-Friendly Interface: The system should have a user-friendly interface that is easy to navigate and understand, even for non-technical users.
- Scalability and Flexibility: The system should be scalable and flexible to accommodate your business’s changing needs.
Benefits of Using CRM with Blacklist Monitoring
Implementing a CRM with blacklist monitoring offers numerous benefits, including:
- Enhanced Risk Management: Proactively identify and mitigate potential risks associated with high-risk customers.
- Improved Regulatory Compliance: Meet KYC and AML requirements and avoid costly penalties.
- Strengthened Brand Reputation: Protect your brand image by avoiding association with individuals or entities involved in illegal activities.
- Reduced Financial Losses: Minimize the risk of financial losses due to fraud, money laundering, or other illegal activities.
- Increased Efficiency: Automate the blacklist screening process and free up valuable time for compliance officers and other personnel.
- Better Customer Insights: Gain a deeper understanding of your customer base and identify potential risks before they escalate.
- Competitive Advantage: Demonstrate your commitment to compliance and risk management, which can attract and retain customers.
Challenges and Considerations
While CRM with blacklist monitoring offers significant benefits, there are also some challenges and considerations to keep in mind:
- Data Accuracy: Blacklists are not always perfectly accurate, and false positives can occur. It is important to have a process in place to verify the accuracy of matches and avoid taking action based on inaccurate information.
- Data Privacy: Blacklist screening involves processing sensitive personal data, so it is important to comply with data privacy regulations, such as GDPR and CCPA.
- Implementation Costs: Implementing a CRM with blacklist monitoring can be expensive, especially if you need to integrate with multiple blacklist data providers.
- Ongoing Maintenance: Blacklists are constantly updated, so it is important to ensure that your CRM system is kept up-to-date with the latest information.
- Integration Complexity: Integrating a CRM system with blacklist data providers can be technically complex, requiring expertise in data integration and security.
Choosing the Right CRM with Blacklist Monitoring Solution
Selecting the right CRM with blacklist monitoring solution is a critical decision. Consider these factors:
- Business Needs: Carefully assess your specific business needs and regulatory requirements. What types of risks are you most concerned about? Which blacklists are most relevant to your industry?
- Vendor Reputation: Choose a reputable vendor with a proven track record of providing reliable and secure CRM solutions.
- Blacklist Coverage: Ensure that the CRM system supports the blacklists that are most relevant to your business.
- Integration Capabilities: Verify that the CRM system can integrate with your existing systems and processes.
- Pricing: Compare the pricing of different CRM solutions and choose one that fits your budget.
- Customer Support: Look for a vendor that offers excellent customer support and training.
Conclusion
In today’s complex and regulated business environment, CRM with blacklist monitoring is an essential tool for protecting your reputation, ensuring regulatory compliance, and mitigating financial risks. By integrating blacklist monitoring into your CRM system, you can proactively identify and avoid potentially damaging interactions with high-risk individuals or entities, safeguarding your business from legal penalties, reputational damage, and financial losses. Choosing the right solution and implementing it effectively is a key step in building a resilient and trustworthy business. Remember to prioritize data accuracy, privacy compliance, and ongoing maintenance to maximize the benefits of this powerful technology.